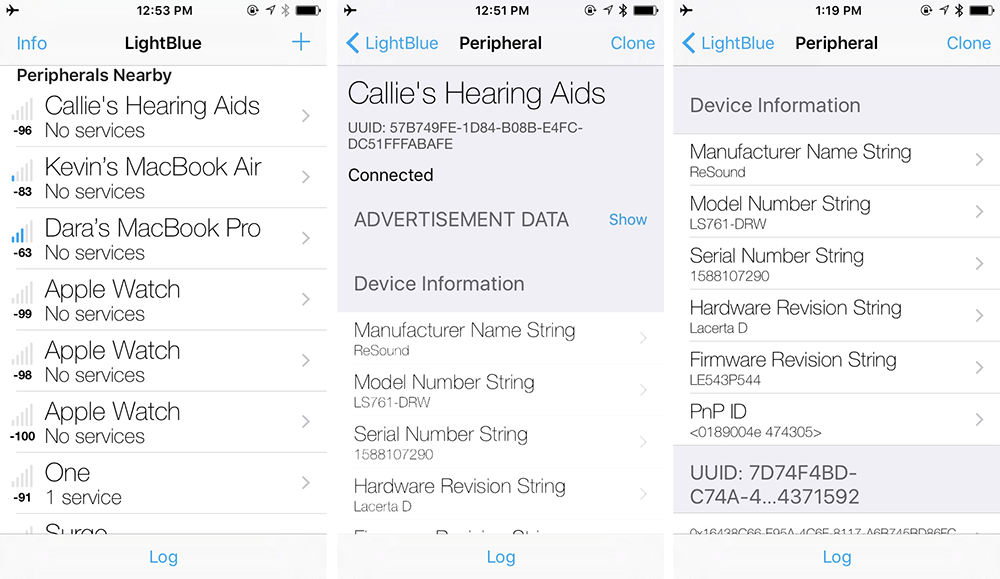
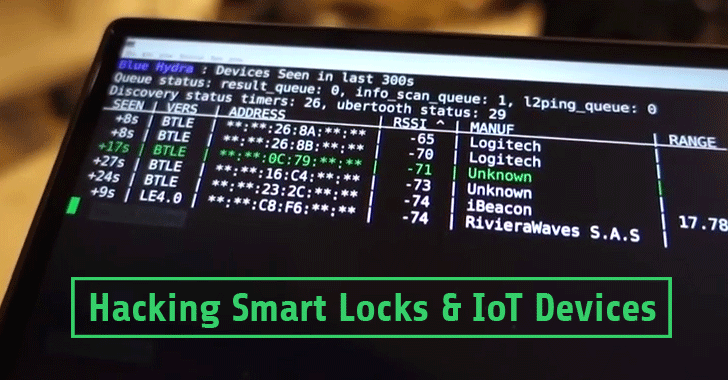
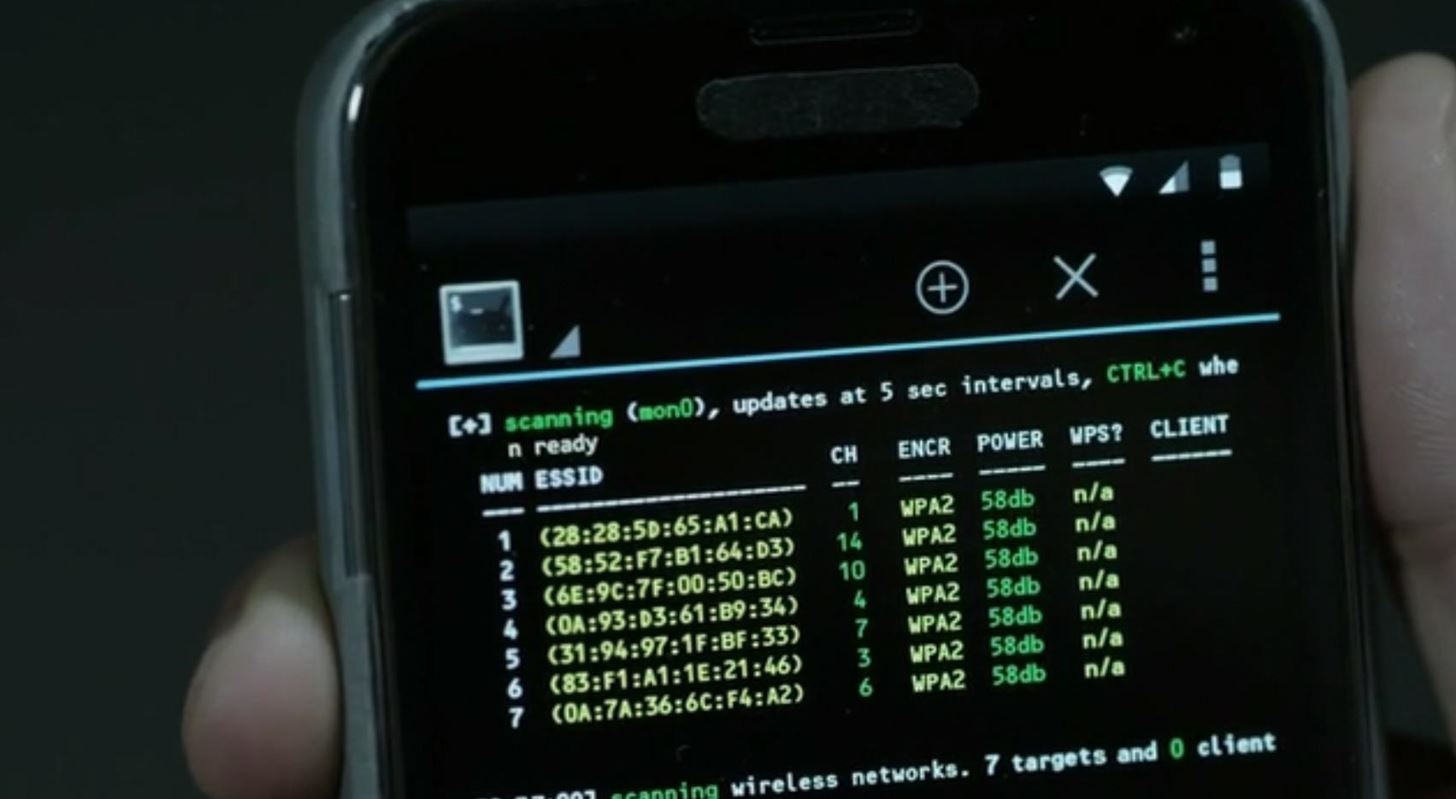
Using TWS or Bluetooth devices? Here's how you can safeguard yourself from Bluetooth hacking - India Today

How to hack Android, macOS, iOS, and Linux through a Bluetooth vulnerability | Kaspersky official blog

Different Bluetooth Hacking Techniques That You Should Know To Prevent Loss Of Data | Cyware Alerts - Hacker News